逆向日期:2024.02.06
使用工具:Node.js
文章全程已做去敏处理!!! 【需要做的可联系我】
可使用AES进行解密处理(直接解密即可):在线AES加解密工具
1、打开某某网站(请使用文章开头的AES在线工具解密):T9mpG48zIdYFB40hkjsQS4+N5rr4x4mSPHlx5EoT/+s=
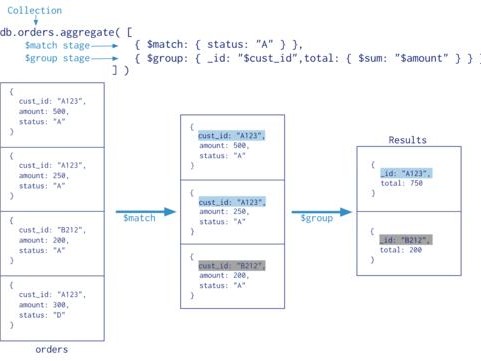
2、点击右上角的登录按钮,账号随便11位即可,密码随便,验证码输入,点击登录后可在控制台的网络面板进行查看

3、ctrl+shift+F全局搜索【poaaword】,经过我七七八百天终于找到了,他在这里被加密,其中【W】参数位固定值,【l】参数为10位整数的时间戳,【a.data.password】为明文
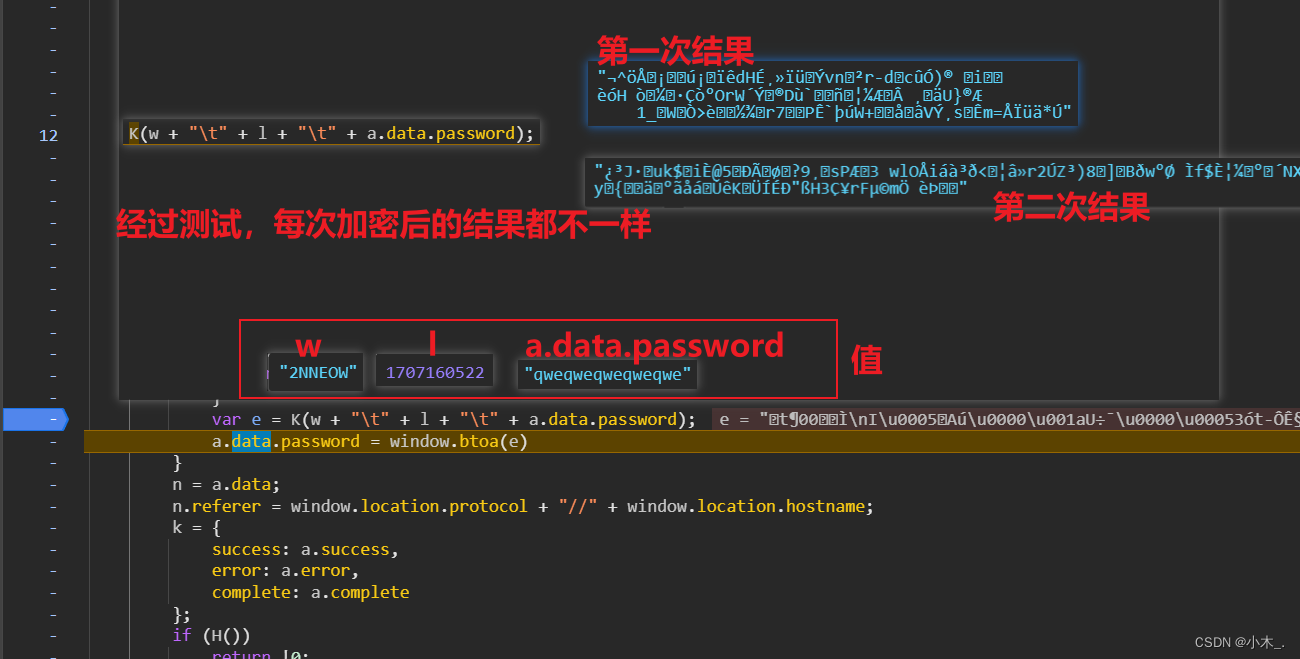
4、我在控制台调用【K】加密函数,发现每次加密结果都不一样,要么是RSA加密,要么就是里面有时间戳,我们直接单步进【K】函数
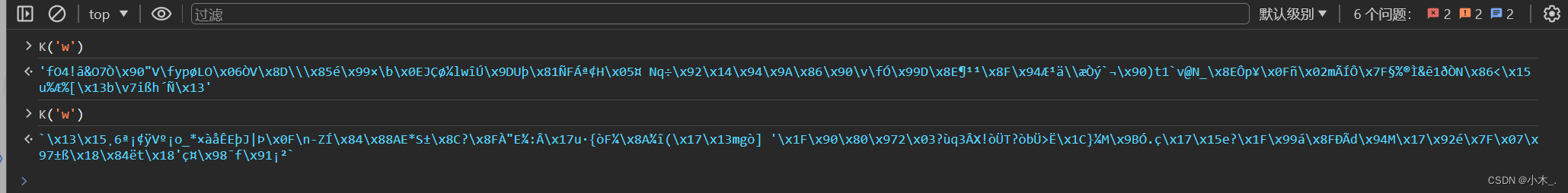
5、通过【K】参数进来后,发现就在刚刚加密参数的下面,一大堆,好像是被拆散了,这种也看不出来是什么加密 ,直接扣他源代码就行

6、扣下来后直接调用运行,发现有报错,报错显示【f】参数未定义,我们去源代码瞅瞅
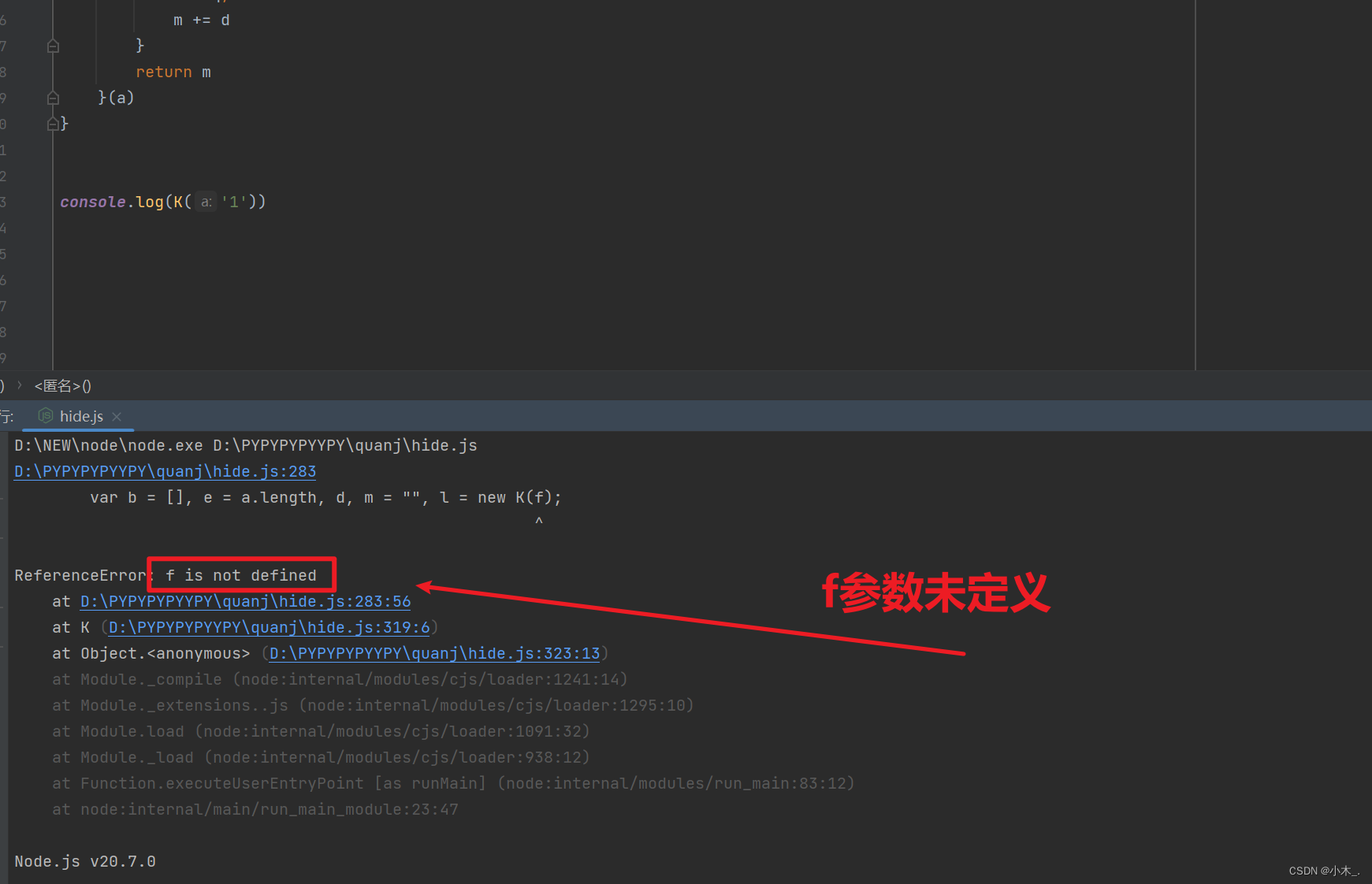
7、在源代码里发现【f】参数是一个key,但这也不能证明此网站的加密方法是RSA,也有可能是DES或AES,因为里面好像有时间戳,所有导致每次加密的结果都不一样,那我们直接把key复制到我们代码里
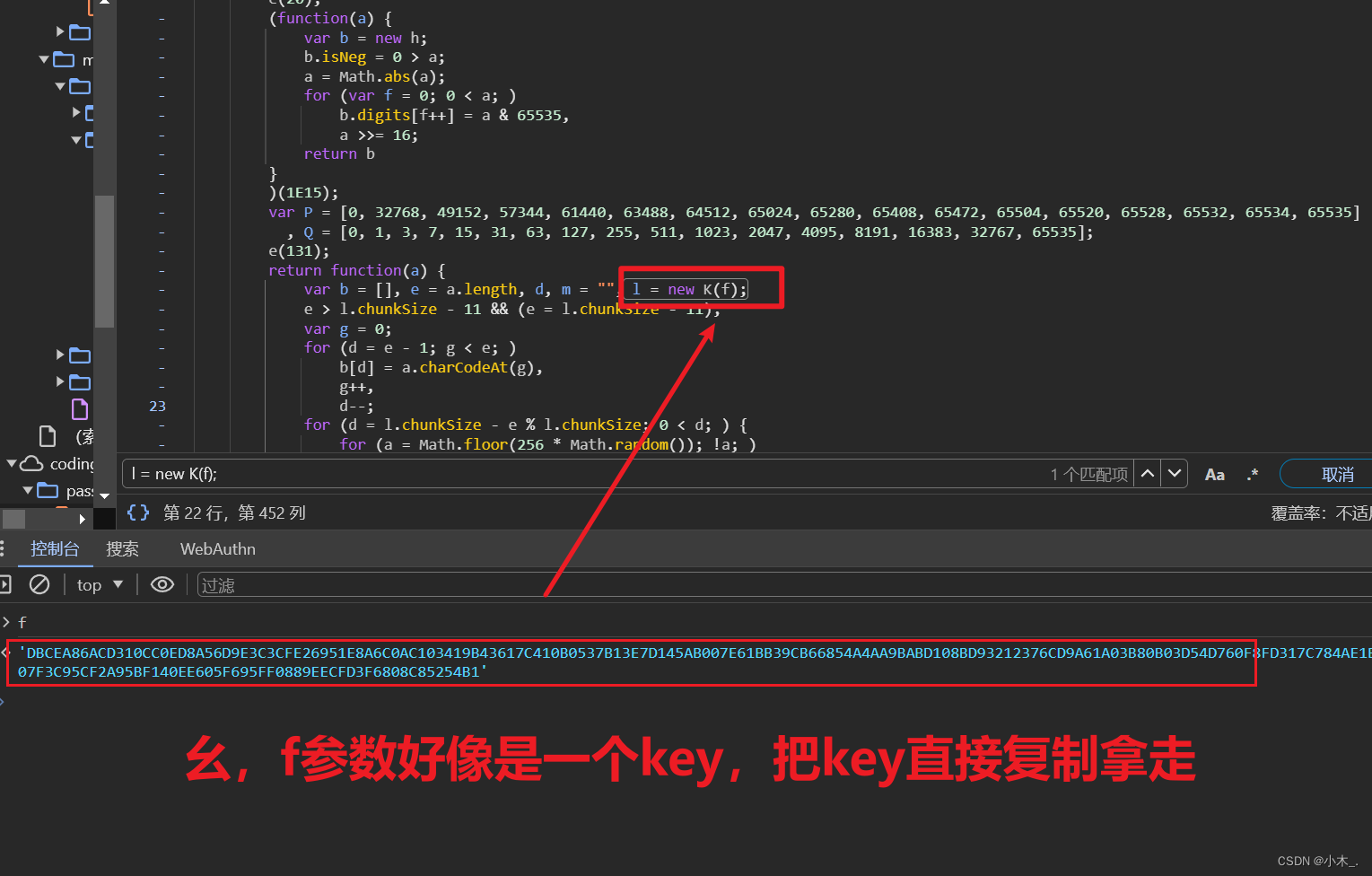
8、幺,成了,把key拿过来后,加密成功了,而且每次的加密结果都不一样,我们还差用【btoa】加密一下就欧克了,btoa是内置函数,可以直接调用,我们直接在代码里添加即可

9、看结果,加密三次都是不一样的结果,哎这就成了
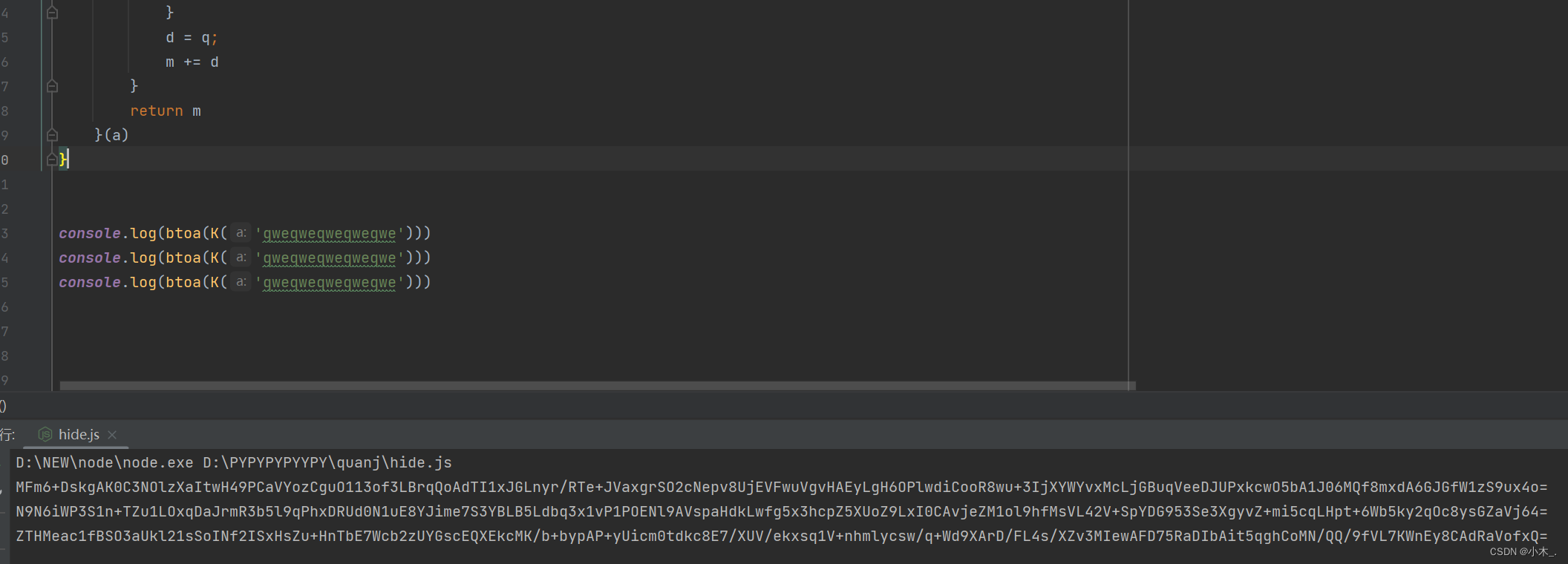
【附上源码】
为防止二次编辑或对该网站的原创保护,只能将源代码进行混淆展示。
var G=function(_0xbe0570){function _0xfbf4e(_0x43b580){_0x4c40b3=_0x43b580;_0x205846=Array(_0x4c40b3);for(_0x43b580=0x8968d^0x8968d;_0x43b580_0x3c1d6d;)--_0x27d8f7["\u0064\u0069\u0067\u0069\u0074\u0073"][_0x574137-_0x38e274-(0x23a23^0x23a22)],_0x4b0073=_0x27d8f7["\u0064\u0069\u0067\u0069\u0074\u0073"][_0x574137-_0x38e274-0x1]*(0x10000*_0x375b2c|_0x274b7e),_0x3c1d6d=0x100000000*_0x402d89+(0x10000*_0x29b5c8+_0x22f49b);_0x22f49b=_0x402d89=_0xae6678(_0x14e496,_0x574137-_0x38e274-(0x8710c^0x8710d));_0x375b2c=_0x27d8f7['digits'][_0x574137-_0x38e274-0x1];result=new _0x298ae8();_0x29b5c8=_0x181d13(_0x22f49b);for(_0x274b7e=_0x4b0073=0x23b0b^0x23b0b;_0x274b7e>>=0x502cc^0x502dc;result['digits'][0x1+_0x29b5c8]=_0x4b0073;_0x14dddd=_0x57a6b1(_0x14dddd,result);_0x14dddd["\u0069\u0073\u004e\u0065\u0067"]&&(_0x14dddd=_0x28a2f0(_0x14dddd,_0x402d89),--_0x27d8f7['digits'][_0x574137-_0x38e274-0x1]);}_0x14dddd=_0x579545(_0x14dddd,_0x5f5804);_0x27d8f7['isNeg']=_0xb919f9['isNeg']!=_0x3c50d3;_0xb919f9['isNeg']&&(_0x27d8f7=_0x3c50d3?_0x28a2f0(_0x27d8f7,_0x1eb173):_0x57a6b1(_0x27d8f7,_0x1eb173),_0x14e496=_0x579545(_0x14e496,_0x5f5804),_0x14dddd=_0x57a6b1(_0x14e496,_0x14dddd));0x0==_0x14dddd['digits'][0x0]&&(0x3d9c8^0x3d9c8)==_0x181d13(_0x14dddd)&&(_0x14dddd['isNeg']=!0x1);}_0xb919f9=[_0x27d8f7,_0x14dddd];this['mu']=_0xb919f9[0xf1b7e^0xf1b7e];this['bkplus1']=new _0x298ae8();this["\u0062\u006b\u0070\u006c\u0075\u0073\u0031"]['digits'][this['k']+(0x9c005^0x9c004)]=0x1;this["\u006d\u006f\u0064\u0075\u006c\u006f"]=_0xd71242;this['multiplyMod']=_0x37405f;this['powMod']=_0x2c31c5;}function _0xd71242(_0x51f621){var _0x2f2f48=_0x5196fc(_0x51f621,this['k']-0x1);_0x2f2f48=_0xed7ff9(_0x2f2f48,this['mu']);_0x2f2f48=_0x5196fc(_0x2f2f48,this['k']+0x1);_0x51f621=_0x270bcd(_0x51f621,this['k']+0x1);_0x2f2f48=_0xed7ff9(_0x2f2f48,this['modulus']);_0x2f2f48=_0x270bcd(_0x2f2f48,this['k']+(0x8762e^0x8762f));_0x51f621=_0x57a6b1(_0x51f621,_0x2f2f48);_0x51f621["\u0069\u0073\u004e\u0065\u0067"]&&(_0x51f621=_0x28a2f0(_0x51f621,this["\u0062\u006b\u0070\u006c\u0075\u0073\u0031"]));for(_0x2f2f48=(0xda443^0xda443)=0x10;return _0x126518;})(0x38d7ea4c68000);var _0x33740a=[0x72078^0x72078,0x8000,0xb2f05^0xbef05,0xe000,0x75571^0x7a571,0x93fd9^0x9c7d9,0x218a8^0x2e4a8,0xfe00,0xff00,0xbacde^0xb535e,0xffc0,0x8e59c^0x81a7c,0xfff0,0xfff8,0xfffc,0xfffe,0xffff],_0x29ca19=[0x0,0x1,0x781cd^0x781ce,0x7,0xf,0x1f,0x6d84b^0x6d874,0x7f,0xb38e8^0xb3817,0x1ff,0x33628^0x335d7,0x7ff,0xfff,0x1fff,0x3fff,0x7fff,0xffff];_0xfbf4e(0x83);return function(_0x27e0d7){var _0x1397f8=[],_0x4a80f7=_0x27e0d7["\u006c\u0065\u006e\u0067\u0074\u0068"],_0x53dde5,_0x21ef1f="".split("").reverse().join(""),_0x3083f9=new _0x1968b6("1B45258C8086F3DFCEE9880FF596F506EE041FB59A2FC59C3F70FCEFC4F92ED62535C4BB334FC7FBEE64937F3FCBA0983D2A9848B1EA487C713DF8F067D45D30B08B30A16A9DC67321239DB801DBAB9AA4A45866BC93BB16E700BA541D7E31B7350B014C71634B914301CA0C6A8E15962EFC3C3E9D65A8DE0CC013DCA68AECBD".split("").reverse().join(""));_0x4a80f7>_0x3083f9["\u0063\u0068\u0075\u006e\u006b\u0053\u0069\u007a\u0065"]-(0xaee6c^0xaee67)&&(_0x4a80f7=_0x3083f9['chunkSize']-0xb);var _0x2518e4=0x0;for(_0x53dde5=_0x4a80f7-(0xb471a^0xb471b);_0x2518e4