docker仓库登录及配置insecure-registries的方法
这篇文章主要介绍了docker仓库登录配置insecure-registries的方法,docker客户端如果配置中添加了insecure-registary配置,就不需要在docker 客户端配置上对应证书,如果不配置要在/etc/docker/certs.d/目录中添加对应证书才能正常登录,感兴趣的朋友跟随小编一起看看吧
−
目录
- 1. 配置/etc/docker/daemon.json
- 2. 配置systemd启动文件
- docker client insecure-registries配置
1. 配置/etc/docker/daemon.json
1
2
3
4
5
# cat /etc/docker/daemon.json
{
"registry-mirrors": ["https://0nth4654.mirror.aliyuncs.com"],
"insecure-registries": ["harbor.domain.io"]
}
2. 配置systemd启动文件
和方法1配置会有冲突,不可同时配置
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
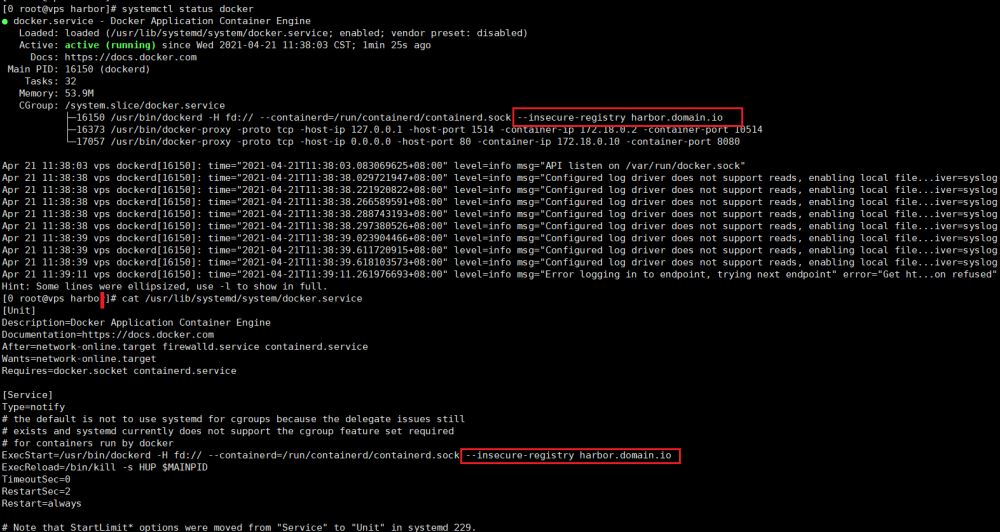
[0 root@vps harbor]# cat /usr/lib/systemd/system/docker.service
[Unit]
Description=Docker Application Container Engine
Documentation=https://docs.docker.com
After=network-online.target firewalld.service containerd.service
Wants=network-online.target
Requires=docker.Socket containerd.service
[Service]
Type=notify
# the default is not to use systemd for cgroups because the delegate issues still
# exists and systemd currently does not support the cgroup feature set required
# for containers run by docker
ExecStart=/usr/bin/dockerd -H fd:// --containerd=/run/containerd/containerd.sock --insecure-registry harbor.domain.io
ExecReload=/bin/kill -s HUP $MAINPID
TimeoutSec=0
RestartSec=2
Restart=always
docker client insecure-registries配置
- docker客户端如果配置中添加了insecure-registary配置,就不需要在docker 客户端配置上对应证书
- 如果不配置就需要在/etc/docker/certs.d/目录中添加对应证书才能正常登录
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
[0 root@vps harbor.domain.io]# docker login harbor.domain.io
Username: admin
Password:
Error response from daemon: Get https://harbor.domain.io/v2/: x509: certificate signed by unknown authority
[1 root@vps harbor.domain.io]# cp /data/secret/certs/harbor.domain.io.crt .
[0 root@vps harbor.domain.io]# docker login harbor.domain.io
Username: admin
Password:
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded
[0 root@vps ~]# cat /root/.docker/config.json
{
"auths": {
"harbor.domain.io": {
"auth": "YWRtaW46cm9vdC4xMjM0"
}
}
[0 root@vps harbor.domain.io]# systemctl status docker
● docker.service - Docker Application Container Engine
Loaded: loaded (/usr/lib/systemd/system/docker.service; enabled; vendor preset: disabled)
Active: active (running) since Wed 2021-04-21 15:06:49 CST; 9min ago
Docs: https://docs.docker.com
Main PID: 32439 (dockerd)
Tasks: 39
Memory: 63.4M
CGroup: /system.slice/docker.service
├─ 920 /usr/bin/docker-proxy -proto tcp -host-ip 0.0.0.0 -host-port 443 -container-ip 172.18.0.10 -container-port 8443
├─ 932 /usr/bin/docker-proxy -proto tcp -host-ip 0.0.0.0 -host-port 80 -container-ip 172.18.0.10 -container-port 8080
├─32439 /usr/bin/dockerd -H fd:// --containerd=/run/containerd/containerd.sock
└─32646 /usr/bin/docker-proxy -proto tcp -host-ip 127.0.0.1 -host-port 1514 -container-ip 172.18.0.2 -container-port 10514
...

到此这篇关于docker仓库登录 配置insecure-registries的文章就介绍到这了








